With each passing day, the challenges for cybersecurity experts are increasing as the attack on users’ networks and computers are not limited to malware, worm, or Trojan, etc. There are spyware and ransomware that can destroy your computer and make it unusable. It is hard to recognize a virus file as they are standard programs that execute on your machine, but with malicious intent. For example, a hacker may put spyware that runs in a stealth manner and provides access to a hacker inside your computer or network.
The symptoms of any corruption in Windows is recognized by the abnormal behavior of computer files or account-
- The computer crashes abruptly after showing a blue screen error.
- The computer runs out of memory even when few programs are running.
- Many programs become too slow to open and execute that was working fine until recently.
- Some unknown programs start to run automatically during the boot process.
- Your account refuses your correct password or changes it without giving any warning.
Windows 10 has accumulated all the possible threats that can occur in the system and crash it beyond repair. So, you should use several security features that will protect you from attacks in advance.
Windows Defender Smart Screen
The Windows Defender Smart Screen stops the threat at first sight. It forbids the users from opening a website that is termed ‘malicious’ or stops such downloads that do not clear its filter criteria. It fights against scamming sites, phishing, fake ads, and drive-by attacks.
User Account Control
User Account Control makes the management of the whole computer much better by running all the applications and tasks under a security context. It checks that which application is authorized by the user and which is not. So, malware or spyware will not even start and corrupt the stem. Although, the administrator can check the filter and allow safe-looking and healthy processes. It reduces the chances of accidental changes to a minimum.
Windows Defender Application Guard
Windows Defender Application Guard provides security to Microsoft Edge Web Browser. It uses Hyper-V Virtualization technology to whitelist the site and show them as trusted sites. When the site is not trusted, then Application Guard opens it in a secure container excluding access to memory, store, endpoints, and other applications.
Microsoft Bitlocker
It is a full-end encryption solution provided to Professionals and business enterprises. It expands the file and system protection and makes the data inaccessible when the computer is decommissioned.
Windows Defender Credential Guard
Defender Credential Guard provides software access to only privileged users. It uses virtualization-based security to assess the rightful users who are authorized by the administrator to run some programs. For example, in a shared computer, the administrator can block some users from running Exchange Server.
If you are not using any of the above-mentioned security features, then your computer may face corruption, and many files may become affected by it. If you are also facing such corruption, then use the following methods to repair the affected file or sector.
Run sfc scan
System File Checker (sfc) is the inbuilt utility feature that checks the system file for supposed corruption and shows you the affected area. If you can run it in the command prompt as an Administrator.
and click Enter.
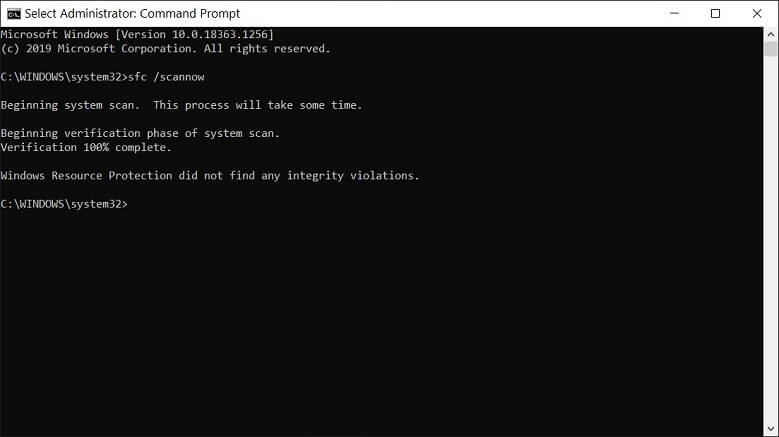
The process will take some time to complete and show any errors in the system file.
Run SFC in safe mode
If the sfc scan does not complete the process or show the correct problem, then you can try to run in safe mode.
- Restart the computer and go to the Troubleshoot mode.
- Click Advanced options, then Startup Settings, and choose to restart.
- Choose the safe mode to boot the computer and run the command prompt as the Administrator.
- Type sfc /scannow option.
Restore Windows 10
The System Restore is an inbuilt service that helps you to restore Windows to a previous state leaving the changes committed after it. In the restore feature, you choose a time that works as the restoration point. If you suspect that corruption in Windows is new, then you can restore it to a select point. Here is how you can create it-
- Type restore point in the search bar and click it.
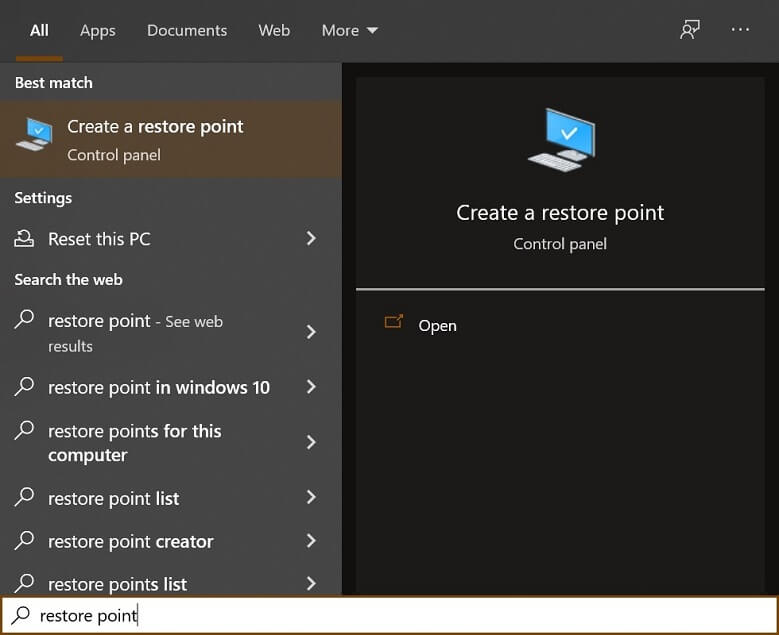
- Click the System Restore option under the System Protection tab.
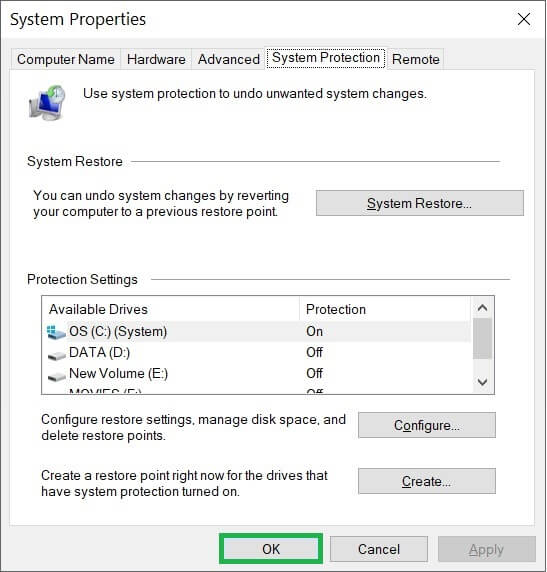
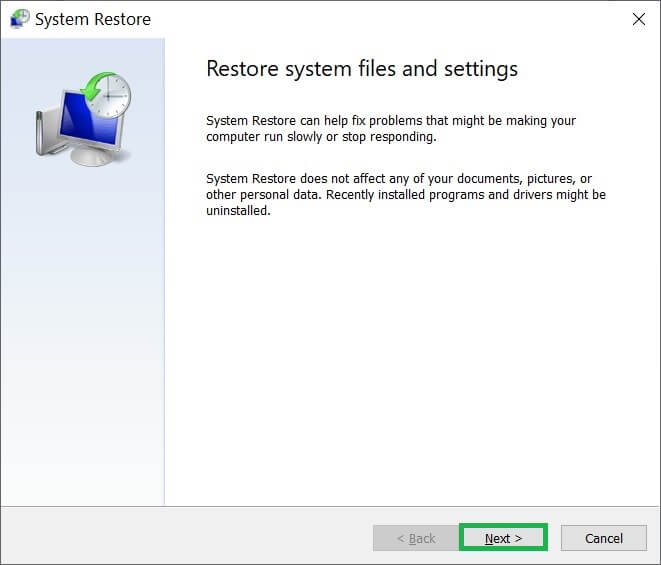
- Click Next in the System Restores wizard.
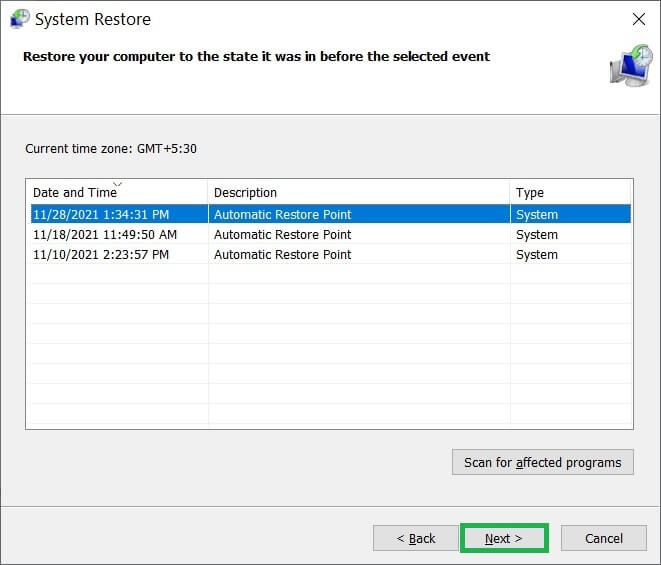
- Choose the time at the restore point and click Next.
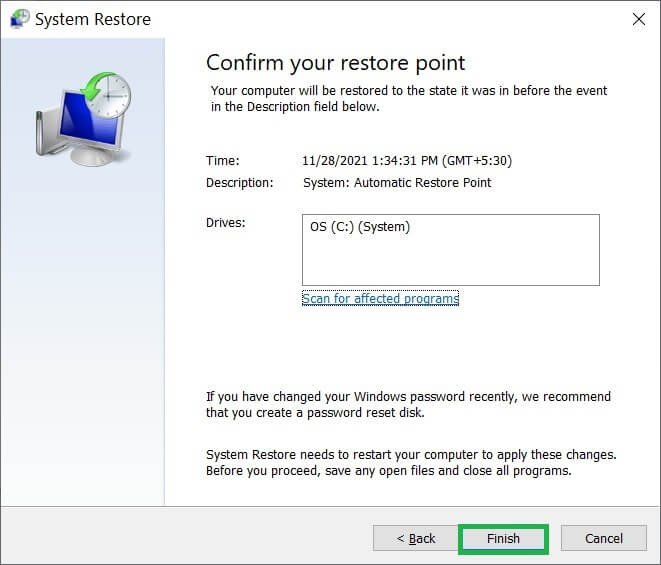
- Confirm your restoration point by clicking the Finish button.
Restore Windows 10
When some system files are corrupt beyond repair, then you should restore the Windows completely.
- Then click the Power button, keep the shift button and choose Restart.
- Choose Troubleshoot>>Reset this PC. Choose either of the options – keep my files or remove everything.
- Input the username and password of your account and click Reset.
- Complete the process to Reset your PC.
Conclusion
When the system registry files are corrupt, then you cannot help your Windows by using any recovery or restore method. So, you can use the second alternate to recover the content of the corrupt Windows system. Use a professional Windows Repair software that can repair corruption and recover items. You should use the software to recover complete items and save them on a different computer.